Applications rarely function as isolated islands. Instead, they communicate constantly with other software systems to exchange data, trigger actions, and deliver seamless user experiences.
At the core of this communication infrastructure lies the API (Application Programming Interface) - the invisible connective tissue enabling applications to interact.
Third-party APIs have fundamentally changed the economics of software development for startups and established enterprises alike. A small team can now create applications with capabilities that would have required dozens of specialized engineers just a decade ago.
This democratization of technology has fueled innovation across industries, enabling companies to focus resources on their unique value proposition rather than rebuilding standard functionalities.
Understanding APIs: The Basics
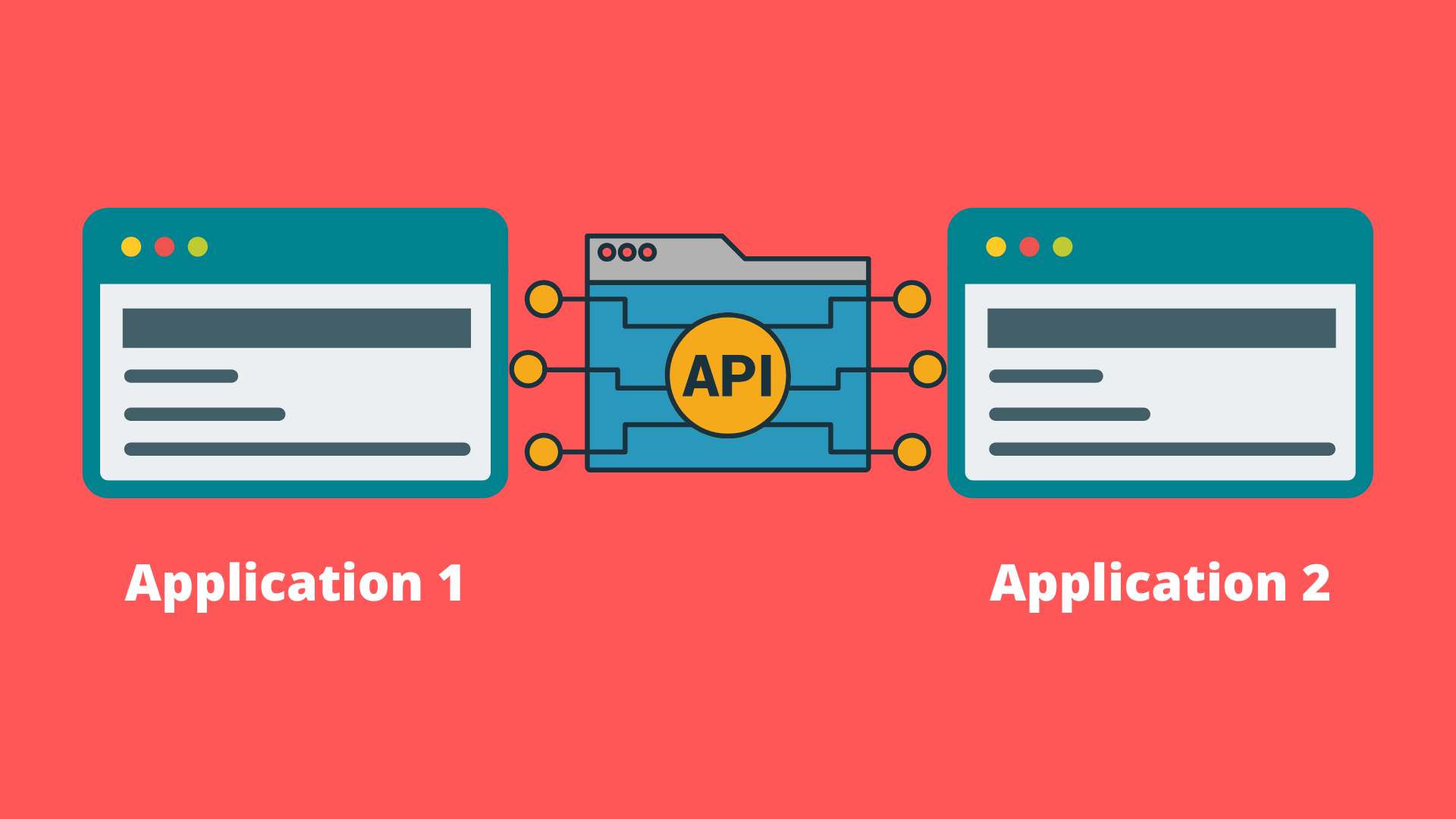
At their core, Application Programming Interfaces (APIs) serve as messengers that deliver your request to a provider and then return the response to you. They are sets of rules and protocols that allow different software applications to communicate with each other, defining the methods and data formats that applications can use to request and exchange information.
Canva, Canva Pro license
APIs work on a request-response model. When an application sends a request to an API endpoint, the API processes this request according to its defined rules and returns the appropriate response. This communication happens through standardized protocols, with the most common being:
- REST (Representational State Transfer): A lightweight architectural style that uses HTTP methods like GET, POST, PUT, and DELETE. REST APIs are stateless and separate the client and server concerns, making them highly scalable. They typically return data in JSON or XML format.
- GraphQL: A query language for APIs that allows clients to request the needed data. Unlike REST, which might require multiple endpoints for different data needs, GraphQL uses a single endpoint where clients specify their data requirements in the request.
- SOAP (Simple Object Access Protocol): A more rigid protocol that uses XML for message formatting and typically operates over HTTP or SMTP. SOAP provides built-in error handling and has strict standards, making it suitable for enterprise environments where security and reliability are paramount.
To understand APIs in simpler terms, think of a restaurant scenario: You (the client) don't go into the kitchen (the system) to prepare your meal. Instead, you interact with the waiter (the API) who takes your order (the request), delivers it to the kitchen, and brings back your food (the response).
The menu serves as documentation, showing what you can order, while the kitchen's processes remain hidden. This separation of concerns allows the restaurant to change its kitchen procedures without affecting how you place orders. APIs enable systems to evolve independently while maintaining consistent client interfaces.
What Are Third-Party APIs?
Third-party APIs are application programming interfaces developed and maintained by external organizations that provide access to their services, data, or functionality. Unlike first-party APIs (which you create for your own applications) or internal APIs (which facilitate communication between your systems), third-party APIs are explicitly designed to allow external developers to integrate with established platforms and services.
At their core, third-party APIs function as pre-built bridges that connect your application to external services, eliminating the need to develop complex functionality from scratch. These interfaces follow standardized protocols like REST, GraphQL, or SOAP, providing structured methods for requesting and receiving data or triggering actions.
Third-party APIs are versatile and span virtually every industry. In e-commerce, payment gateways like Stripe and PayPal handle secure transactions. Social media platforms offer APIs for authentication, content sharing, and analytics. Communication services provide APIs for SMS, email, and voice capabilities.
Mapping services like Google Maps enable location-based features, while financial institutions offer APIs for banking operations and market data. AI capabilities can be accessed through third-party APIs like OpenAI or Google Cloud.
First-Party vs. Third-Party: Key Differences
When building modern applications, developers often have to choose between creating their own APIs or leveraging existing third-party solutions. This decision impacts everything from development timelines to long-term maintenance strategies.
Ownership differences
First-party APIs are developed and maintained by your own organization. You retain complete ownership of the code, data flow, and implementation details. In contrast, third-party APIs belong to external providers who control the underlying infrastructure, data processing, and access policies.
With first-party APIs, your organization maintains intellectual property rights and can potentially monetize the API as a product. Third-party APIs operate under licensing agreements that may restrict how you use their services and often prohibit reselling or redistributing their functionality.
Control and customization capabilities
Third-party APIs provide standardized functionality with limited customization options. While many offer configuration settings and parameters, you're ultimately constrained by the provider's implementation decisions. This trade-off sacrifices perfect alignment with your needs for rapid implementation of proven solutions.
Reliability and dependency factors
When using third-party APIs, you introduce external dependencies into your application architecture:
| Factor | First-party APIs | Third-party APIs |
|---|---|---|
| Uptime control | Complete internal control | Dependent on provider's reliability |
| Service changes | Scheduled on your timeline | May change with limited notice |
| Versioning | Managed according to your needs | Provider determines deprecation schedule |
| Rate limits | Self-determined based on capacity | Set by provider, may require premium tiers |
| Troubleshooting | Direct access to logs and systems | Limited visibility into underlying issues |
A third-party API outage can render your application wholly or partially non-functional, creating a single point of failure outside your control. While not immune to problems, first-party APIs allow your team to diagnose and resolve issues immediately.
API Authentication and Security
API security is a critical aspect of modern application development, acting as the gatekeeper that protects valuable data and functionality from unauthorized access. At the heart of this security framework lies a robust authentication and authorization system that ensures only legitimate users can interact with your API endpoints.
The purpose and management of API keys
API keys serve as the primary identification mechanism for applications accessing an API. These unique alphanumeric strings function like digital passports, allowing API providers to:
- Identify the calling application and track its usage patterns
- Control access to specific API features and resources
- Enforce rate limits to prevent abuse and ensure fair usage
- Monitor consumption for billing and analytical purposes
Unlike simple passwords, API keys are designed for programmatic access. They typically don't expire unless manually revoked, making them ideal for long-running applications. However, this persistence also presents security challenges, requiring careful management practices:
- Store keys in environment variables or secure vaults, never in code repositories
- Implement key rotation policies to replace older keys periodically
- Use different keys for development, testing, and production environments
- Establish procedures for immediate key revocation when compromised
Authentication vs. Authorization
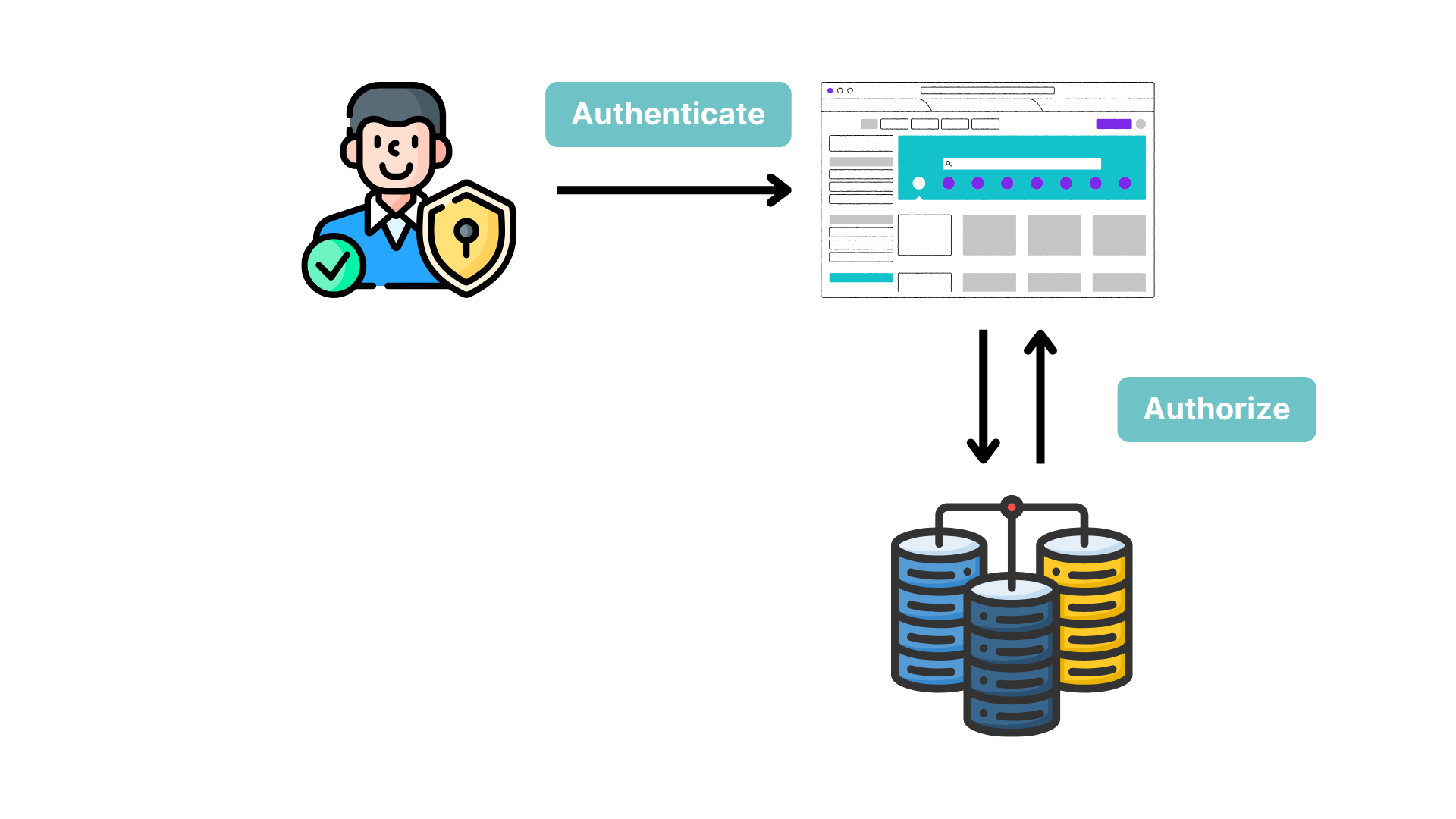
While often mentioned together, authentication and authorization serve distinct purposes in API security:
Authentication answers the question "Who are you?" It verifies the identity of the user or application making the request. This process confirms that the requester is who they claim to be, typically through:
- API keys
- Username/password combinations
- Digital certificates
- Biometric verification
Authorization addresses "What are you allowed to do?" Once identity is established, authorization determines what resources the authenticated entity can access and what actions they can perform. Authorization mechanisms include:
- Role-based access control (RBAC)
- Attribute-based access control (ABAC)
- Permission sets and scopes
- Resource-level permissions
A well-designed API implements both processes: first, authenticating the requester and then authorizing specific actions based on their verified identity.
Common security protocols
Modern APIs rely on several standardized protocols to implement secure authentication and authorization:
OAuth 2.0
OAuth 2.0 has become the industry standard for API authorization. It enables third-party applications to access user resources without exposing credentials. The workflow typically involves:
- The application requests authorization from the user
- The user approves the request
- The authorization server issues an access token
- The application uses the token to access protected resources
OAuth 2.0 supports various "grant types" for different scenarios, including authorization code flow for web applications, implicit flow for browser-based apps, and client credentials for server-to-server communication.
JSON web tokens (JWT)
JWTs provide a compact, self-contained method for securely transmitting information between parties. These tokens consist of three parts:
- Header: Identifies the algorithm used for signing
- Payload: Contains claims about the entity and additional metadata
- Signature: Verifies the token hasn't been altered
JWTs excel in stateless authentication scenarios where session management on the server side is impractical. They can encode user identity, roles, and permissions directly within the token, reducing database lookups.
Bearer tokens
Bearer tokens are simple access tokens that grant access to whoever possesses them, hence the name "bearer." They're commonly used with OAuth 2.0 and typically implemented as JWTs. While convenient, their simplicity means possession alone grants access, making secure transmission essential.
Popular Third-Party APIs Across Industries
The modern digital landscape is powered by a vast ecosystem of specialized APIs that serve virtually every industry vertical. These third-party solutions have become the building blocks for today's applications, enabling developers to integrate sophisticated functionality without starting from scratch.
Payment processing APIs
Payment processing APIs have revolutionized e-commerce and digital transactions by abstracting away the complexity of financial operations.
Stripe offers one of the most developer-friendly payment APIs, supporting everything from simple one-time transactions to complex subscription models and marketplace payments.
Stripe's robust documentation and testing environment allow developers to implement secure payment flows in hours rather than weeks. It handles PCI compliance and fraud detection and supports payment methods across more than 135 currencies.
PayPal remains a trusted payment solution with global recognition. Its APIs enable everything from standard checkout experiences to advanced features like recurring billing, micropayments, and mass payouts.
PayPal's adaptive payments API allows for complex scenarios like split payments and chained transactions, making it particularly valuable for marketplaces and platforms.
Mapping services
Location intelligence has become critical for applications across numerous sectors, from transportation to retail.
Google Maps Platform provides the most comprehensive mapping solution with APIs for static and dynamic maps, street view, routes, places, and geolocation. Its strength lies in its global coverage, accurate data, and familiar user interface. Applications can customize map styles, add markers and overlays, and calculate optimal routes with real-time traffic considerations.
Social media integration
Social media APIs enable applications to connect with popular platforms for authentication, content sharing, and community building.
Facebook Graph API provides access to Facebook's social graph, allowing applications to read and write data to Facebook. This includes user profiles, posts, photos, events, and pages. The API enables social login functionality, content sharing, and the ability to retrieve social context that can personalize user experiences.
Twitter/X API allows applications to access tweets, user profiles, and trending topics. Developers can implement features like displaying relevant tweets, posting updates, and analyzing sentiment or engagement metrics.
Benefits of Implementing Third-Party APIs
Faster development
Implementing third-party APIs dramatically accelerates development timelines. According to industry benchmarks, development teams can reduce project timelines by 60-70% when using established APIs instead of building functionality from scratch.
For example, integrating a payment processing API takes 2-3 days, while building an in-house payment system requires 3-6 months of development.
Cost-benefit analysis
The financial advantages of third-party APIs extend beyond obvious development savings:
| Cost factor | In-House development | Third-Party API |
|---|---|---|
| Initial development | 50,000-$300,000+ | $0-5,000 |
| Ongoing maintenance | 5,000-20,000/month | Often included in subscription |
| Specialized talent | Required | Not required |
| Infrastructure | Self-managed | Provider-managed |
Advanced features
Third-party APIs provide immediate access to specialized technologies that would otherwise require significant expertise to develop:
- AI and machine learning: Natural language processing, image recognition, and predictive analytics APIs from providers like OpenAI or Google Cloud ML enable advanced capabilities without requiring data science teams.
- Geospatial services: Location intelligence, routing algorithms, and mapping visualizations through APIs like Google Maps or Mapbox.
- Communications: SMS, voice, video, and chat functionality through Twilio, Vonage, or similar providers.
These technologies often represent years of research and development that would be impractical to replicate internally.
Challenges of Third-Party APIs
While third-party APIs offer tremendous benefits, they also introduce significant risks that the app development expert team must carefully manage. Forward-looking teams increasingly partner with a web application development company to treat API design as part of a broader platform strategy, rather than a series of ad hoc technical decisions.
Integrating external services into your application's core functionality creates dependencies affecting your product's stability, scalability, and long-term viability.
Service reliability concerns
The most immediate risk of third-party API dependency is reliability. When you integrate an external API, you're essentially placing part of your application's functionality in someone else's hands:
- Unexpected downtime: If the API provider experiences server issues or outages, your application's dependent features will fail, even if your infrastructure functions perfectly.
- Performance fluctuations: API response times may vary based on the provider's server load, network conditions, or maintenance activities, creating inconsistent user experiences.
- Rate limiting: Most APIs impose request limits that can throttle your application during peak usage, potentially causing failures precisely when your service is most in demand.
Customization limitations
Third-party APIs are designed to serve many customers, which inherently limits customization options:
- Fixed functionality: You're restricted to the features and capabilities the provider chooses to offer.
- Limited flexibility: Request and response formats, authentication methods, and endpoint behaviors are standardized and rarely customizable.
- Workflow constraints: Your application must adapt to the API's workflow rather than the API adapting to your ideal process.
Security and compliance considerations
When integrating third-party APIs into your applications, security and compliance become critical concerns that extend beyond your own infrastructure. Your application inherits the security posture of every API it connects with, creating an expanded attack surface that requires careful management.
Data privacy concerns
Third-party APIs often process sensitive user data, raising significant privacy concerns:
- Data transmission: Information traveling between your application and third-party services may be intercepted if proper encryption isn't implemented
- Data storage: You have limited visibility into how API providers store your users' data
- Data usage: Third parties might use customer data for purposes beyond your intended use case
- Data ownership: Confusion can arise about who ultimately owns data processed through external APIs
Always review the API provider's privacy policy and data handling practices to address these concerns. Implement data minimization principles by only sharing what's necessary with third-party services.
Security audit recommendations
Before and during third-party API integration, conduct these security assessments:
- Penetration testing: Simulate attacks against API endpoints to identify vulnerabilities
- Code reviews: Examine how your application implements API calls and handles responses
- Dependency scanning: Check for known vulnerabilities in API client libraries
- Authentication review: Verify proper implementation of authentication mechanisms
- Regular compliance audits: Schedule periodic reviews to ensure ongoing compliance
Request the API provider's SOC 2 reports or similar security certifications to verify their security practices meet industry standards.
Vendor lock-in problems
Once you've built your application around a specific third-party API, changing providers becomes increasingly complex:
- Deep integration: APIs often become deeply woven into application architecture, making extraction challenging without significant refactoring.
- Unique features: Proprietary features of one API may not have direct equivalents in competing services, complicating migration.
- Business logic dependency: Over time, your business logic may become tightly coupled with the API's specific implementation details.
Tools for API Integration
The complexity of working with multiple third-party APIs has given rise to specialized tools that streamline integration, testing, and management. These tools have become essential for developers and web application development firms looking to leverage external APIs efficiently.
- Postman: The industry standard for API testing, featuring intuitive request building, automated testing, mock servers, and collaboration tools
- Zapier: Connect over 3,000 apps without coding, automating workflows between services
- RapidAPI: Discover or publish APIs.
These platforms democratize API integration, allowing non-technical teams to create connections between services without developer intervention.
Conclusion: Maximizing Value from Third-Party APIs
Third-party APIs have firmly established themselves as the backbone of modern digital connectivity, enabling businesses of all sizes to accelerate innovation and expand capabilities without reinventing the wheel. Throughout this exploration, we've seen how these powerful tools can transform development cycles, reduce costs, and unlock advanced functionality that would otherwise remain out of reach.
The key to success lies in strategic implementation. Organizations that approach third-party API integration with careful planning, evaluate security implications, consider scalability needs, and assess vendor reliability position themselves to reap maximum benefits while minimizing potential disruptions. This balanced approach acknowledges both the tremendous advantages APIs offer and the dependencies they create.
Looking forward, businesses should adopt future-proofing strategies for their API implementations:
- Maintain a flexible architecture that can accommodate API changes or replacements
- Implement robust monitoring systems to identify and respond to API performance issues quickly
- Develop contingency plans for critical API dependencies
- Stay informed about API roadmaps and upcoming changes from providers
- Consider a multi-vendor approach for mission-critical functions
As the API economy expands, the organizations that thrive will view APIs not merely as technical tools but as strategic assets in their digital ecosystem. By thoughtfully selecting, implementing, and managing third-party APIs, businesses can harness external innovation while maintaining control over their technological destiny.
Aug 27, 2025
